This blog entry is a replication of my previous blog entry: Tomcat – Container Managed Security. It is extending the same entry for JBoss, so I’m gonna skip all the introduction and straight-away get to work.
Basic Authentication
1. Open the login-config.xml file located at ${JBOSS_HOME}/server/${USER_PROFILE}/conf
This file sets up the configuration for the security domains available to applications running in the server. JBoss uses JAAS for the underlying security infrastructure, and JAAS interacts with a security store for authenticating credentials.
In simple words, we specify an application policy in this file, which tells the Login Module that we will use (Like Tomcat, here also we have plenty of options like LDAP, Database, Property Files etc for Login Modules). Basically, Login Module specifies the usernames, passwords and roles used for protecting your application. To start with, we will use UsersRolesLoginModule, which uses a property file to specify all the above mentioned information. Obviously, this isn’t secure and not really a choice for a system in production. Time to make changes:
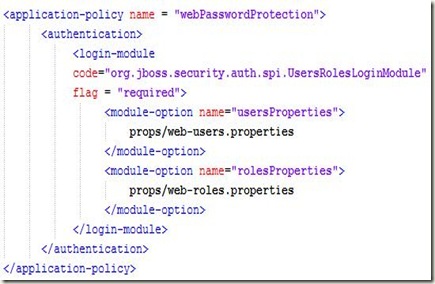
Make changes in login-config.xml file : Add the following policy at the end of the file:
- The "name" attribute on the "application-policy" element specifies the name of the security domain. This name is important because it is what will be used to tie the security domain to the web application later. We will mention it in application’s web.xml.
- The "login-module" element specifies the login module that this domain will use.
- The "module-option" elements specify some values to pass into the login module's "initialize" method. For UserRolesLoginModule, we will specify the property files for user information and role information. These paths are relative to the ${JBOSS_HOME}/server/${USER_PROFILE}/conf directory.
2. Open the ${jboss.dist}/server/${server.name}/conf/props and create 2 files:
- web-users.properties (user information)
- web-roles.properties (role information)
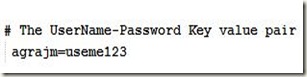
In web-users.properties property file, add
In web-roles.properties, add
3. Open web.xml of your web application and make following changes -- add following security constraint:
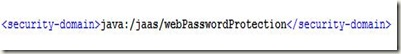
4. Open jboss-web.xml of your web application and add following line inside the <jboss-web> element:
This element tells JBoss to connect the web application to the "webPasswordProtection" security domain (application policy) we defined in the login-config.xml file earlier. JBoss exposes security domains via JNDI by pre-pending "java:/jaas/" to the name element in the application-policy element in the login-config.xml file.
Voila!! You are done now. Just restart the JBoss Server and your authentication should work fine.
DIGEST Authentication
Having already said that this basic authentication is not recommended for production purposes, we will try using a different authentication mechanism : Digest Passwords. We will save the passwords in a digest (hashed) form in the properties file instead of saving them in clear-text form. Make following changes:
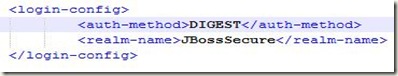
1. Change in login-config.xml file
2. Find the new hashed password using built-in RFC2617Digest class:
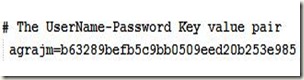
The RFC2617Digest class is present in jbosssx.jar which is present in ${JBOSS_HOME}/server/default/lib directory. So this jar file must be on your classpath when you execute the above command. If it is not so, then use –cp option of java tool to set CLASSPATH as done above. The generated password is b63289befb5c9bb0509eed20b253e985. Note that the arguments passed to this class are
- User Name
- Realm Name
- Password
in that order. Now is the time to store this hashed password in your web-users.properties file.
3. Change web-users.properties file as follows:
Now, just restart JBoss to see the effect. And it is more secure than Basic authentication as you are not transmitting the password over the wire.



No comments:
Post a Comment